Latest
-
Trending
- On the Marxist critique of Heidegger

- Gramsci and his friend “S”

- From Harvard to Karl-Marx-Allee: The Experiences and Reflections of an American Communist in East Germany

- India as a tool to contain China-Geopolitics explained

- The integral crisis in the U.S. and the purity fetish

- Capitalism is the single greatest source of violence

- A Declaration by the American Association of University Professors of Barnard and Columbia

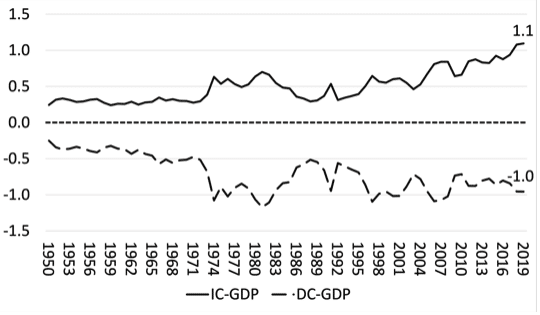
- Further thoughts on the economics of imperialism
- Ukraine war funding and failed Russian sanctions

- Opinion: England’s anti-trans Cass review is politics disguised as science

-
Popular (last 30 days)
- So-Called “Peak China” Is Simply a Western Campaign for China to Commit Economic Suicide

- Marxist theory in Japan: A critical overview

- How CIA and MI6 created ISIS

- On the Marxist critique of Heidegger

- Gramsci and his friend “S”

- “Legacy of Violence: A History of the British Empire” – book review

- Economic Democracy with Pavlina Tcherneva

- Materialism matters: The role of philosophy in science

- Neurodiversity and Justice: Embracing Neurodiversity as Part of the Fight Against Discrimination and Injustice

- U.S. ramps up regime change efforts in Solomon Islands in advance of upcoming election
![[Source: ganjingworld.com]](https://mronline.org/wp-content/uploads/wordpress-popular-posts/151515-featured-75x75.png)